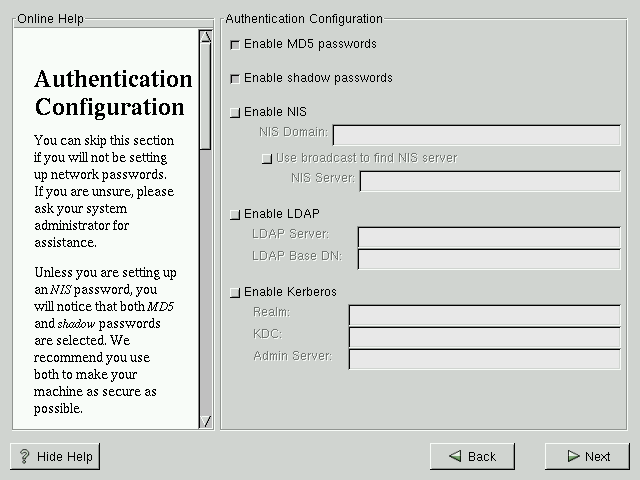
Authentication Configuration
If you are performing a workstation-class installation, please skip ahead to the section called GUI X Configuration Tool.
If you are performing a server-class installation, please skip ahead to the section called Preparing to Install Packages.
You may skip this section if you will not be setting up network passwords. If you are unsure as to whether you should do this, please ask your system administrator for assistance.
Unless you are setting up NIS authentication, you will notice that both MD5 and shadow passwords are selected (see Figure 3-18). We recommend you use both to make your machine as secure as possible.
To configure the NIS option, you must be connected to an NIS network. If you are unsure whether you are connected to an NIS network, please ask your system administrator.
Enable MD5 passwords allows a long password to be used (up to 256 characters), instead of the standard eight letters or less.
Enable shadow passwords provides a secure method of retaining passwords. The passwords are stored in /etc/shadow, which is readable only by root.
Enable NIS allows you to run a group of computers in the same Network Information Service domain with a common password and group file. There are two options to choose from here:
NIS Domain allows you to specify which domain or group of computers your system belongs to.
NIS Server causes your computer to use a specific NIS server, instead of broadcasting a message to the local area network asking for any available server to host your system.
Enable LDAP — the use of LDAP can consolidate certain types of information within your organization. For example, all of the different lists of users within your organization can be merged into one LDAP directory. For more information about LDAP, refer to the Official Red Hat Linux Reference Guide. If you're using LDAP, you should provide these two parameters: LDAP Server and LDAP Base DN.
Enable Kerberos — Kerberos is a secure system for providing network authentication services. For more information about Kerberos, refer to the Official Red Hat Linux Reference Guide. There are three Kerberos-related parameters you'll need to provide here: the Realm, the KDC or Key Distribution Center (KDC), sometimes called a Ticket Granting Server or TGS, and the Admin Server.